
Scrolling through social feeds in Nigeria means your digital footprint grows with every like and comment. Concern about online privacy threats is rising among young adults who value control over their personal information. This guide shows how strategic choices and smart habits can help you protect your digital identity while staying connected on platforms that shape daily life.
Table of Contents
- Defining Online Privacy And Common Myths
- Major Types Of Online Privacy Threats
- How Personal Data Is Collected And Used
- Global Online Privacy Laws And Enforcement
- Risks Of Neglecting Digital Privacy Rights
- Best Practices To Safeguard Your Online Privacy
Key Takeaways
| Point | Details |
|---|---|
| Understanding Online Privacy | Online privacy involves controlling personal information rather than complete anonymity; it’s essential to manage what you share and with whom. |
| Awareness of Privacy Threats | Online privacy threats include data tracking, phishing, and identity theft, and require proactive defense strategies for personal data protection. |
| Personal Data Collection Practices | Both explicit and implicit methods are used to collect personal data, highlighting the need for individuals to remain vigilant about their digital footprints. |
| Implementing Best Practices | Utilize strong passwords, enable two-factor authentication, and regularly audit your digital accounts to enhance your online privacy. |
Defining Online Privacy and Common Myths
Online privacy is more than just a technical concept – it represents your fundamental right to control personal information in the digital world. Emerging privacy research highlights how complex and nuanced privacy definitions have become in our interconnected digital landscape.
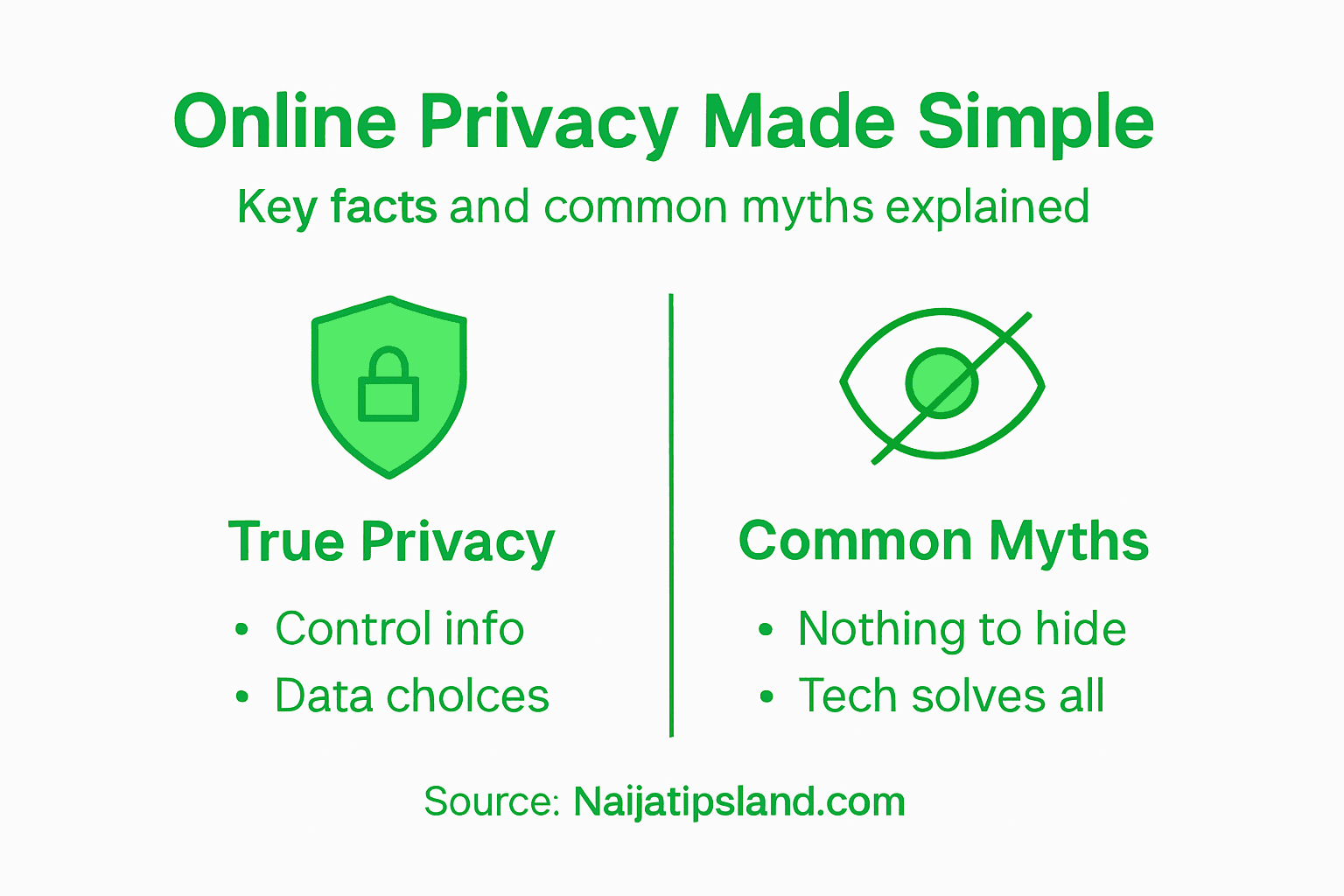
People often misunderstand online privacy, believing it means complete anonymity or total data invisibility. However, privacy is actually about strategic information management – determining what details you share, with whom, and under what circumstances. Academic perspectives on privacy reveal that privacy decisions are rarely straightforward and heavily depend on contextual factors.
Some prevalent myths about online privacy include:
- Privacy means hiding everything
- Only people with something to hide care about privacy
- Corporations always respect user data
- Personal information isn’t valuable
In reality, online privacy involves understanding digital footprints, controlling data exposure, and making informed choices about personal information sharing. Your digital identity is a valuable asset that requires careful protection and strategic management.
Pro tip: Review your social media privacy settings quarterly and conduct a comprehensive audit of your digital accounts to minimize potential information leakage.
Major Types of Online Privacy Threats
Online privacy threats have evolved dramatically, transforming from simple data collection to sophisticated digital surveillance strategies. Privacy research explores emerging risks that threaten personal information security across multiple digital platforms.
The primary categories of online privacy threats can be systematically classified into technical, social, and behavioral risks. These threats range from data breaches and tracking technologies to psychological manipulation and targeted advertising. Comprehensive privacy analysis reveals that most threats exploit individuals’ digital vulnerabilities through sophisticated technological and psychological strategies.
Key types of online privacy threats include:
- Data Tracking: Companies monitor browsing habits, search history, and personal interactions
- Phishing Attacks: Criminal attempts to steal personal credentials through deceptive communications
- Location Surveillance: Continuous tracking of physical movements through mobile devices
- Identity Theft: Unauthorized access and misuse of personal information
- Social Engineering: Psychological manipulation to extract sensitive information
Understanding these threats is crucial for developing effective personal digital protection strategies. Each threat represents a potential breach of your digital autonomy, requiring proactive and strategic defense mechanisms.
For quick reference, here is how major types of online privacy threats differ by approach:
| Threat Type | Typical Attack Vector | Main Vulnerability Exposed |
|---|---|---|
| Technical | Malware, software exploits | Device/data security breach |
| Social | Phishing, social engineering | Psychological and behavioral |
| Behavioral | Data tracking, profiling | Personalized targeting/ads |
This overview helps you recognize which threat is most relevant in different contexts.
Pro tip: Implement multi-factor authentication across all critical digital accounts and regularly update your privacy settings to minimize potential exposure.
How Personal Data Is Collected and Used
Personal data collection represents a complex ecosystem of digital interactions where companies continuously gather information through multiple sophisticated channels. Americans’ data privacy perspectives reveal significant concerns about the extensive methods used to track and monetize individual digital footprints.

The primary mechanisms for personal data collection involve both explicit and implicit methods. Explicit methods include direct form submissions, account registrations, and consent-based data sharing. Implicit methods are more nuanced, involving social media data harvesting through tracking technologies, browser cookies, location services, and behavioral analysis algorithms.
Key data collection strategies encompass:
- Website Tracking: Recording browsing patterns and interaction history
- Mobile App Permissions: Accessing device-specific information
- Social Media Monitoring: Analyzing posts, interactions, and network connections
- Purchase History: Tracking consumer spending and preferences
- Location Services: Monitoring physical movement and geographic data
- Email and Communication Metadata: Collecting communication patterns
Understanding these collection methods empowers individuals to make informed decisions about their digital presence. Each interaction leaves a digital trace that can be potentially collected, analyzed, and monetized by various entities.
Here is a comparison of explicit vs. implicit personal data collection methods:
| Method Type | Example Channel | User Awareness Level | Typical Data Collected |
|---|---|---|---|
| Explicit | Online account registration | High, user actively consents | Email, name, birth date |
| Implicit | Social media tracking | Low, mostly unnoticed | Browsing habits, location, likes |
This table clarifies how your information can be gathered without your full awareness.
Pro tip: Regularly audit app permissions, use private browsing modes, and limit location sharing to minimize unnecessary personal data exposure.
Global Online Privacy Laws and Enforcement
The landscape of online privacy laws represents a complex global framework of regulations designed to protect individual digital rights and regulate data management practices. Data privacy legal frameworks demonstrate significant variations across different national and regional contexts, reflecting unique approaches to digital protection.
The European Union’s General Data Protection Regulation (GDPR) has emerged as the most comprehensive and influential privacy legislation globally, setting stringent standards for data collection, processing, and user consent. Netherlands privacy regulations exemplify how national governments implement and enforce these critical digital protection standards, providing robust mechanisms for citizen data rights.
Key global privacy law characteristics include:
- Consent Requirements: Mandating explicit user permission for data collection
- Right to Erasure: Allowing individuals to request complete data deletion
- Data Breach Notifications: Requiring timely reporting of security incidents
- Cross-Border Data Transfer Restrictions: Limiting international data movement
- Significant Financial Penalties: Imposing substantial fines for non-compliance
- Individual Rights Protection: Empowering users with comprehensive digital control
Effective privacy law enforcement requires ongoing collaboration between governments, technology companies, and international regulatory bodies to adapt to rapidly evolving digital landscapes and emerging technological challenges.
Pro tip: Familiarize yourself with your local data protection laws and understand your rights as a digital citizen to effectively protect your personal information.
Risks of Neglecting Digital Privacy Rights
Neglecting digital privacy rights can trigger profound and far-reaching consequences that extend well beyond simple data exposure. Digital privacy risks reveal complex threats that can fundamentally compromise personal autonomy, financial security, and social standing.
Online privacy research demonstrates that digital privacy negligence can create systemic vulnerabilities affecting both individual and collective security. The risks are multidimensional, impacting personal, professional, and societal domains through sophisticated mechanisms of data exploitation and manipulation.
Key risks of digital privacy neglect include:
- Identity Theft: Unauthorized personal information acquisition
- Financial Fraud: Potential monetary losses through cybercrime
- Professional Reputation Damage: Career opportunities compromised by digital footprints
- Algorithmic Discrimination: Unfair profiling based on collected data
- Psychological Manipulation: Targeted advertising and behavioral engineering
- Surveillance Vulnerability: Increased monitoring by corporations and governments
Understanding these risks transforms privacy from an abstract concept to a critical personal protection strategy. Each digital interaction carries potential long-term consequences that extend far beyond immediate online experiences.
Pro tip: Conduct a comprehensive digital audit of your online accounts, reviewing and minimizing shared personal information to reduce potential exposure risks.
Best Practices to Safeguard Your Online Privacy
Protecting your online privacy requires a strategic and proactive approach that combines technical knowledge with consistent digital hygiene practices. Online privacy protection strategies emphasize the importance of deliberate, informed decisions about digital interactions and personal data management.
Privacy protection techniques reveal that effective online privacy is not about total isolation, but about making smart, calculated choices that minimize unnecessary exposure while maintaining digital connectivity. Understanding and implementing robust protection strategies can significantly reduce potential vulnerabilities.
Key best practices for safeguarding online privacy include:
- Strong Password Management: Use unique, complex passwords for different accounts
- Two Factor Authentication: Enable additional verification methods
- Privacy Browser Settings: Configure browsers to limit tracking
- VPN Usage: Mask your digital location and encrypt internet traffic
- Regular Software Updates: Maintain current security patches
- Minimal Personal Information Sharing: Limit details on public platforms
- Careful App Permission Review: Restrict unnecessary data access
- Periodic Digital Footprint Audit: Regularly review and clean online presence
Effective online privacy protection is an ongoing process that requires consistent attention and adaptive strategies. By implementing these practices, you can significantly reduce your digital vulnerability and maintain greater control over your personal information.
Pro tip: Create a dedicated email address for online registrations to compartmentalize and minimize potential personal data exposure.
Take Control of Your Online Privacy Today
Online privacy challenges are real and constantly evolving. From data tracking to social engineering attacks your personal information is at risk every time you engage online. Understanding these threats and knowing how to protect yourself is essential for preserving your digital autonomy and safeguarding your identity. The article highlights key pain points like identity theft, financial fraud, and psychological manipulation, which demand immediate attention and action.
Naijatipsland.com is more than just a community and news forum. It is your trusted platform to stay informed about the latest developments in online privacy, especially in the Nigerian and broader African context. Engage with other users, share your experiences, and get expert guidance on privacy protection strategies tailored to your environment. Discover relevant discussions and updates that empower you to manage your digital footprint safely and confidently.
Explore current affairs and insights on Naijatipsland.com to learn more about maintaining your privacy in today’s connected world.
Join conversations with other Nigerian internet users and gain practical tips reflected in the article to secure your personal data now.
Stay updated with trusted news and empower yourself with knowledge that transforms your online privacy from vulnerability to strength.
Don’t wait until your privacy is compromised. Visit Naijatipsland.com right now and take the first step towards protecting your online life and digital identity today.
Frequently Asked Questions
What is online privacy, and why is it important?
Online privacy refers to your right to control your personal information in the digital space. It is important because it helps protect your personal identity, data, and digital autonomy from unauthorized access and exploitation.
What are the common myths about online privacy?
Common myths include the belief that privacy means hiding everything, that only people with something to hide care about privacy, and that corporations always respect user data. In reality, online privacy involves making informed choices about what information to share and with whom.
What are major types of online privacy threats to be aware of?
Major threats include data tracking, phishing attacks, location surveillance, identity theft, and social engineering. Each of these poses risks to your personal information and overall security in the digital landscape.
How can I safeguard my online privacy effectively?
You can safeguard your online privacy by using strong password management, enabling two-factor authentication, regularly reviewing app permissions, utilizing VPNs, and conducting periodic audits of your digital footprint.
Recommended
- ‘Social Media Is Not Worth Your Life’ – FRSC Comes Hard On Peller – P.M. News / Naijatipsland
- New York To Require Social Media Platforms To Display Mental Health Labels | Social Media News / Naijatipsland
- ECN Upgrades Information Processing Techniques For Digital Transformation / Naijatipsland
- Why MTN Data Finishes Fast In Nigeria (Real Reasons + Fixes) / Naijatipsland







